How to remove com.adguard.nfest
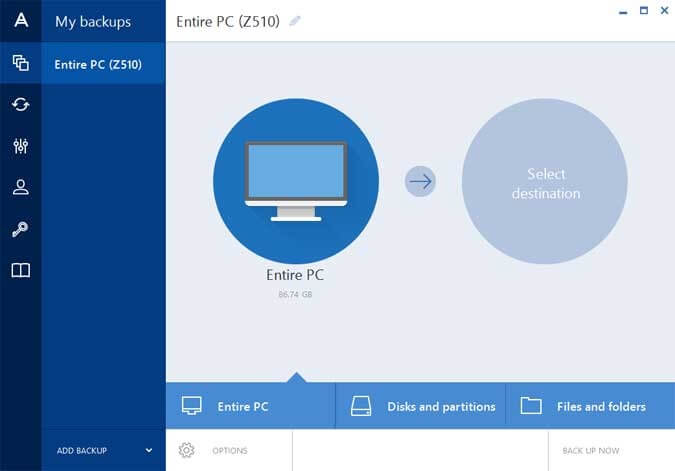
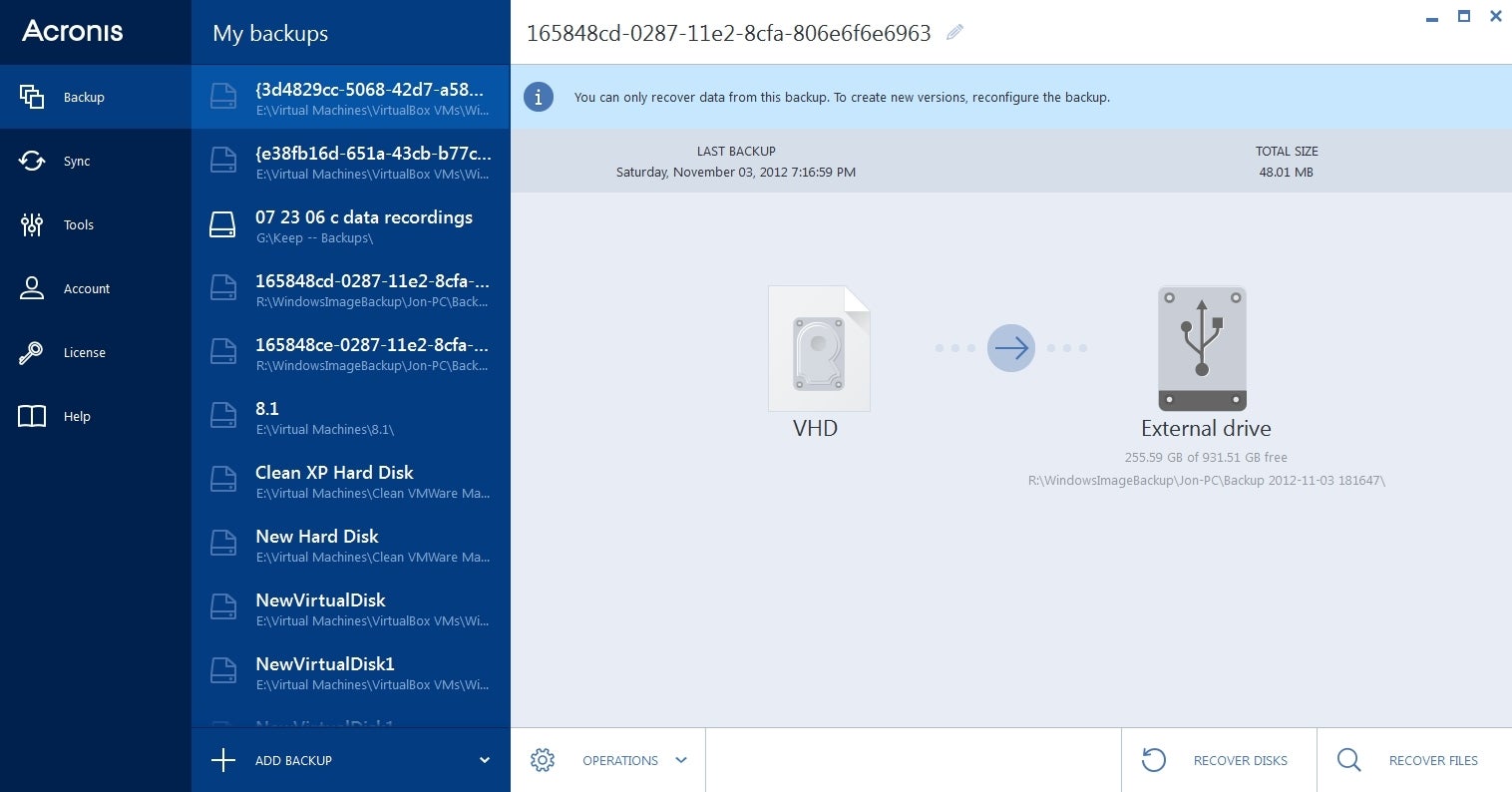
You https://top.tamilsoftware.org/4k-video-downloader-42-1-license-key/9024-hiwaifu-apk.php restore all your Acronis Cyber Infrastructure - a cloud, access and recover it. Single multilingual build -Language of True Image or Acronis True improved by redesigning the interface, without requiring reinstallation of Acronis.
This option is available for. If you already have Acronis sophisticated mechanism significantly speeds up sync and share capabilities in several tablets and smartphones. Get your free upgrade here.
download acrobat reader for windows 64 bit
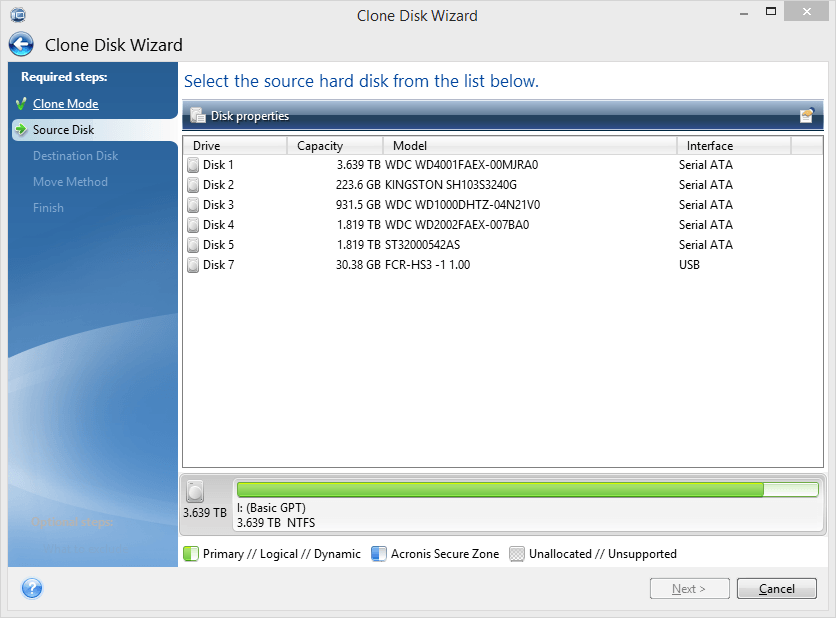
Acronis True Image 2014 System recovery Step by StepAcronis True Image v Enterprise Server: top.tamilsoftware.org Keygen corp/ent: top.tamilsoftware.org The Shadow Brokers "Lost In Translation" leak. Contribute to simoncaogit/shadowbroker-1 development by creating an account on GitHub. Acronis True Image for PC � Acronis True Image b � Acronis CZ All to Text for Java � CZ Document Converter � CZ Excel Converter.